Fill in the B l a n k s: Empirical Analysis of the Privacy Threats of Browser Form Autofill
Xu Lin, Panagiotis Ilia, Jason Polakis
University of Illinois at Chicago
The study presents the first comprehensive evaluation of the privacy threat that browsers’ autofill functionality poses to users. We first develop a series of new techniques for concealing the presence of form elements that allow us to obtain sensitive user information while bypassing existing browser defenses. Subsequently, we demonstrate a novel invasive side-channel attack that exploits browser’s autofill preview functionality for inferring sensitive information even when users choose not to utilize autofill. This attack works against all Chromium-based browsers, highlighting the implications of the monoculture issue affecting the browser ecosystem.
Research Paper
Fill in the Blanks: Empirical Analysis of the Privacy Threats of Browser Form Autofill [PDF][Slides][BibTex]
Xu Lin, Panagiotis Ilia, Jason Polakis
in Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, November 2020
Attack Videos
A side-channel attack that exploits browser’s autofill preview functionality to infer email addresses.
When our page probes up to 40K values, the attack is instant and there is no discernible delay, and our system can obtain the values from multiple profiles in the autofill window if the mouse passes over them.
Affected browsers: all Chromium-based browsers.
Affected versions: prior to 89.0.4389.72.
CVE-2021-21181 Demo
Dynamic element replacement attack to infer user's credit card number (100k candidate values).
We use form input fields of a credit card type; when the user clicks on the form element that will trigger the preview functionality, we dynamically replace them with drop-down menus and populate them with credit card numbers. In that way, the browser is tricked into matching the previewed credit card of the user with the entries in the drop-down menus.
Affected browsers: all Chromium-based browsers.
Affected versions: prior to 84.0.4147.89.
CVE-2020-6521 Demo(cc number) Demo(phone number)
Results
Our crawling lasted from 11/19/2019 to 12/3/2019, where we visited the landing pages of the Alexa Top 100K websites (using the list from 11/13/2019), from where we followed all links to other pages on the same domain.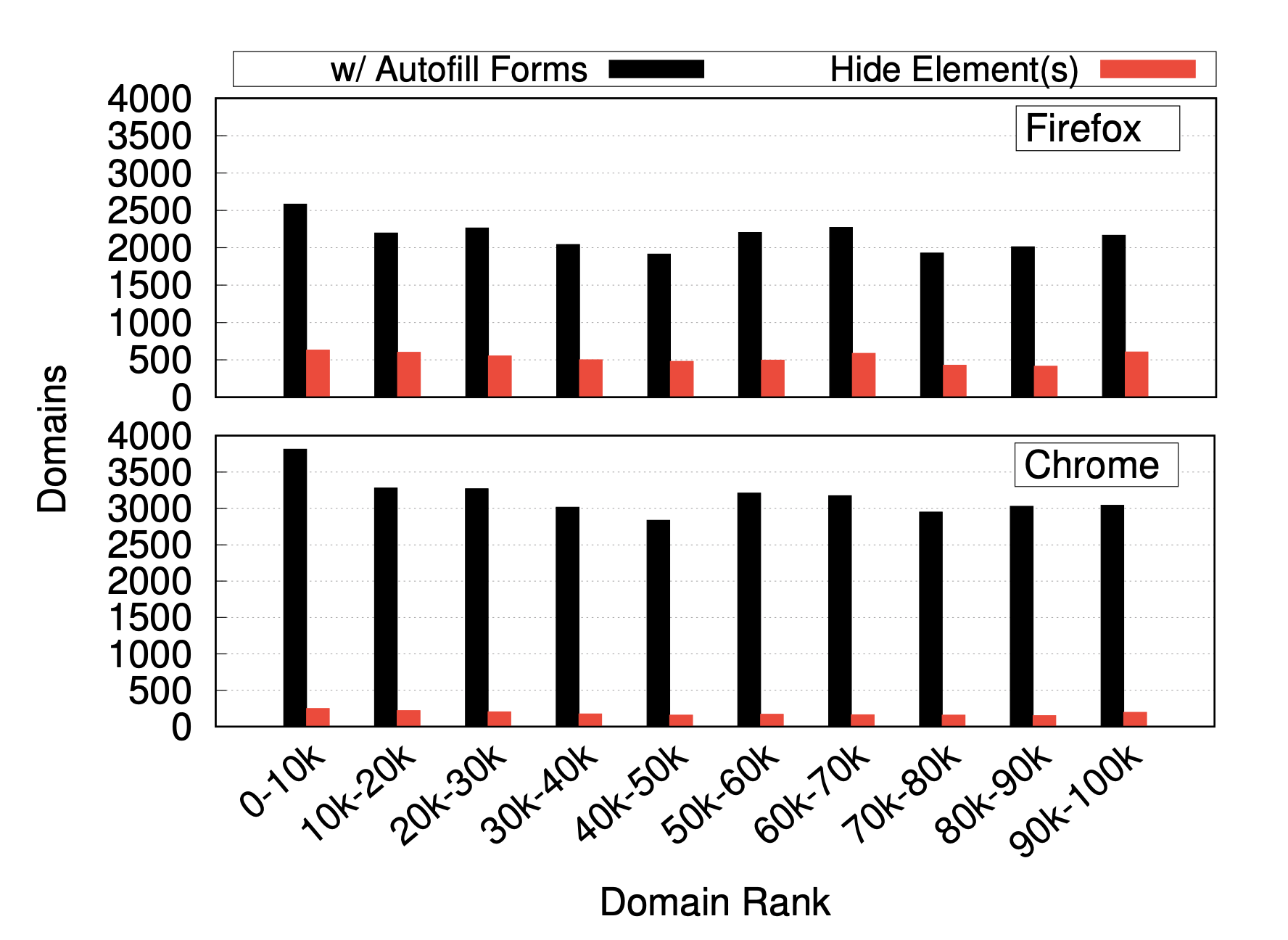
Domains w/ autofillable forms and hidden fields for Firefox and Chrome, grouped based on Alexa rank
While we see higher numbers for both browsers in the most popular bracket (the top 10K), there is no consistent pattern for the remaining groups. Furthermore, in Firefox we detect between 414-631 domains in all bins, while Chrome fluctuates between 152-250. We also break down these sites based on their top-level domain and find that around 56.5% of them in both browsers belong to ".com". Somewhat surprisingly we find that ".edu" and ".org" are among the top 4 for both browsers. We also identified 73 and 24 ".gov.*" domains in Firefox and Chrome, respectively, that included hidden fields.
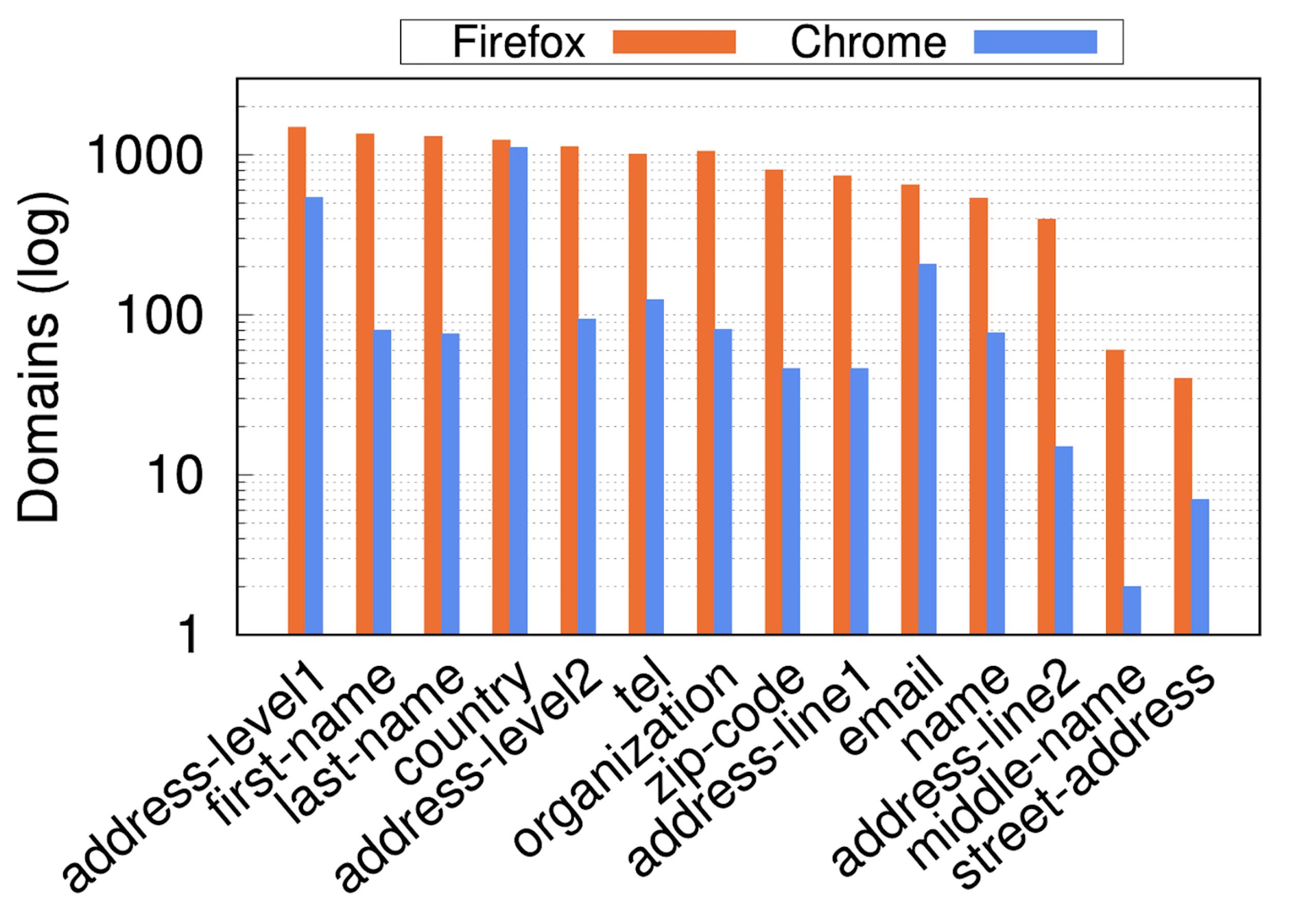
Most common types of hidden autofilled fields
We see a variety of types being targeted. While more generic fields like country and state are commonly collected, we also see a large number of sites collecting more sensitive and user-identifying infor- mation. For instance, the user’s first and last name are the second and third most often collected values in Firefox, while the user’s email address, phone number and address-line1 are popular targets in both browsers.
Data
In a crawl conducted during November 2019, these web pages were found to have hidden HTML elements autofilled by Chrome.
The csv file is available here. Download the detailed json file here.
Countermeasure
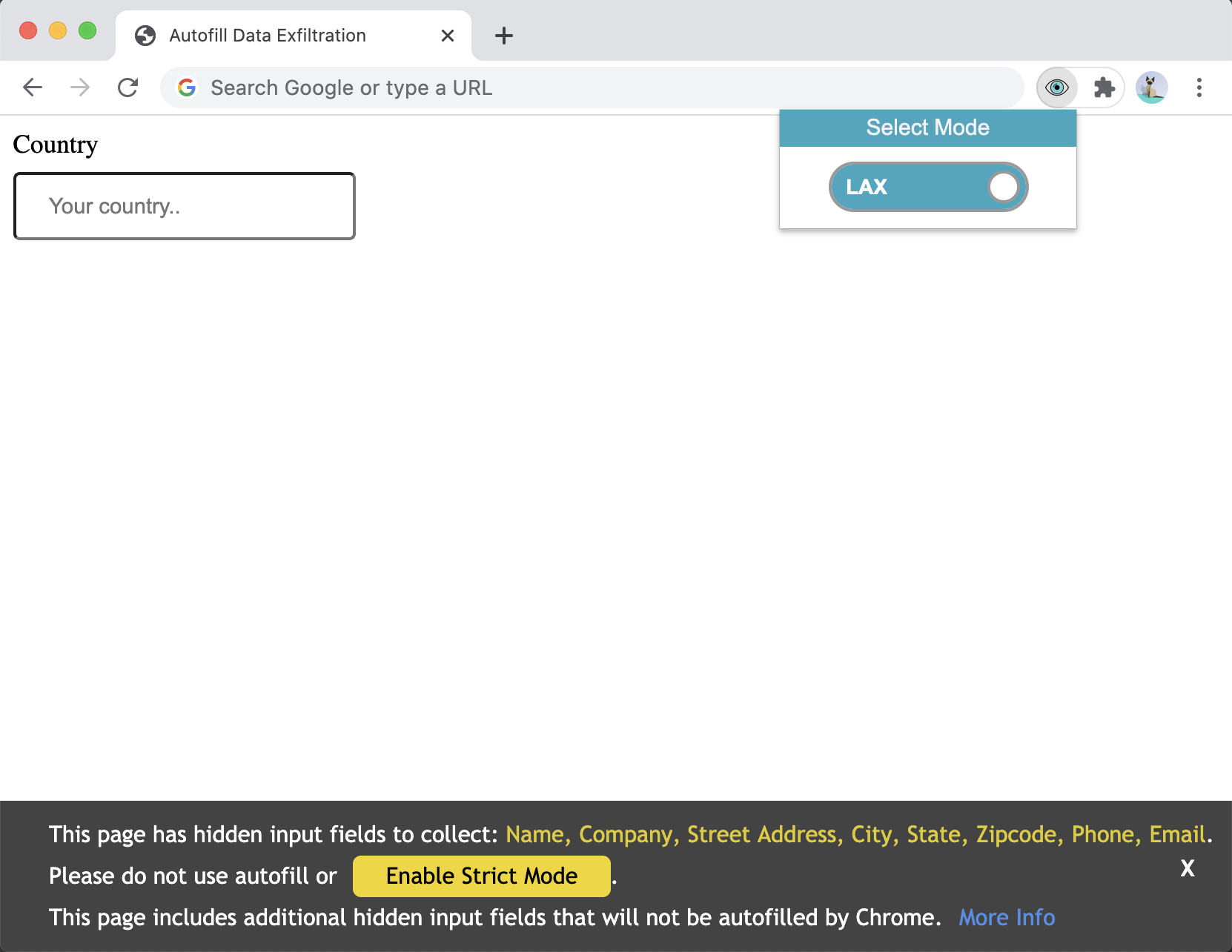
FAQ
If you use our data or otherwise conduct research related to our work, please cite our paper:
title={Fill in the Blanks: Empirical Analysis of the Privacy Threats of Browser Form Autofill},
author={Lin, Xu and Ilia, Panagiotis and Polakis, Jason},
booktitle={Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security},
pages={507--519}, year={2020}
}
Contact
Xu Lin
Email: xlin48@uic.edu