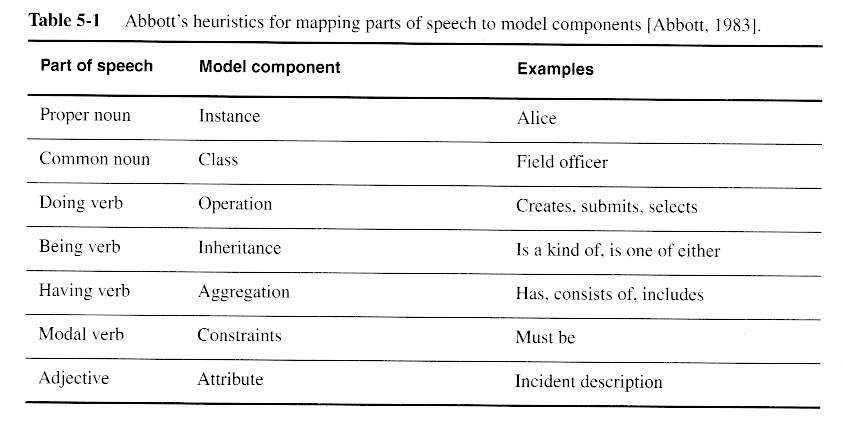
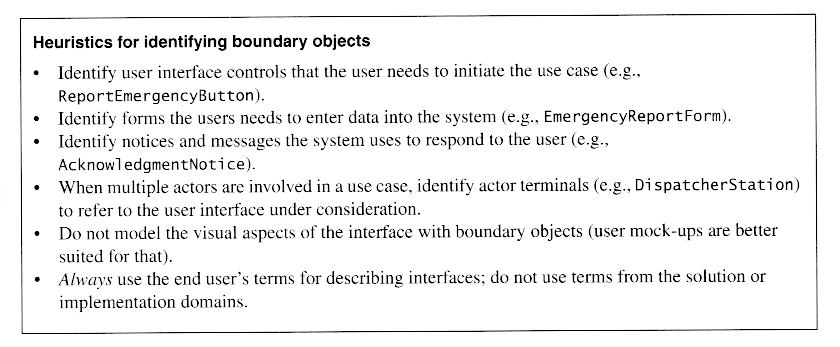
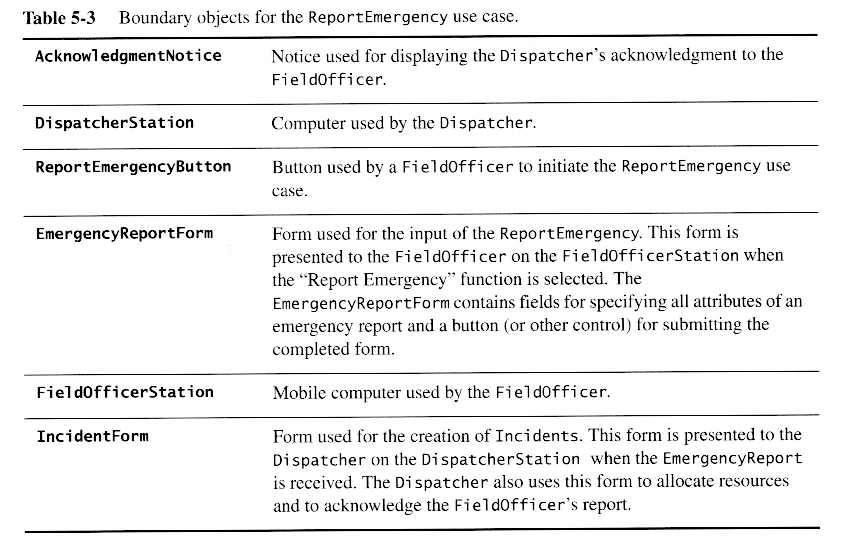
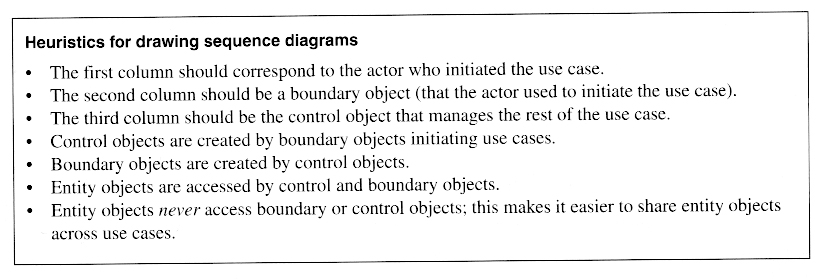
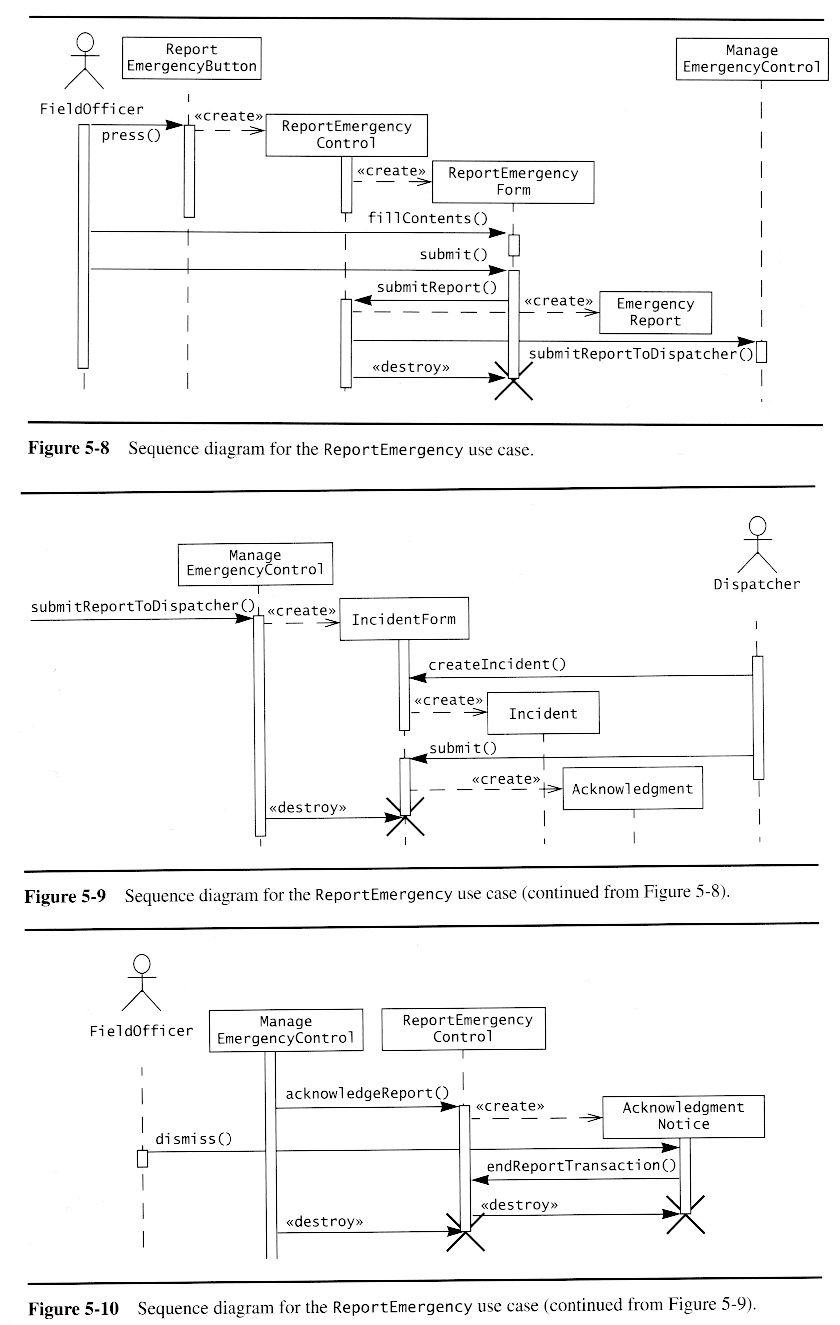
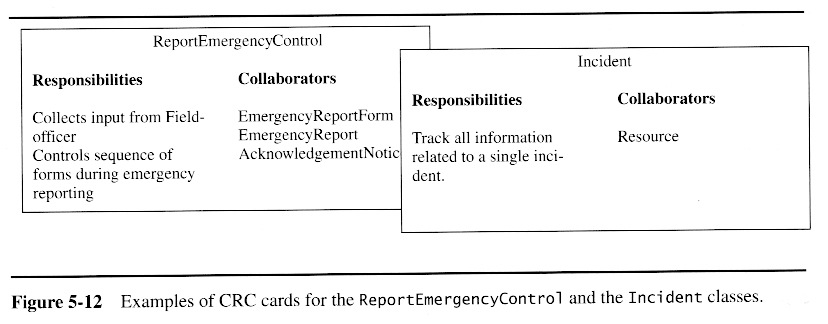
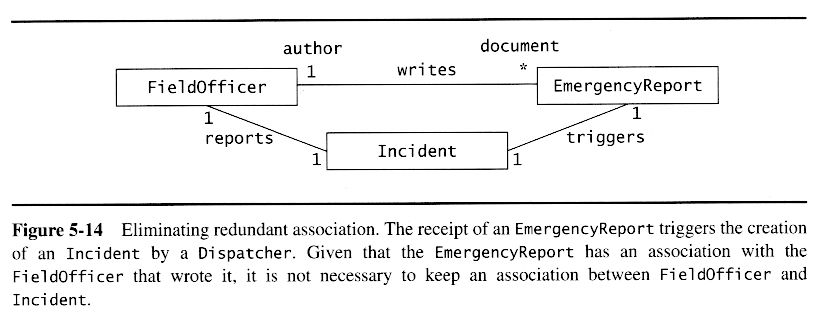
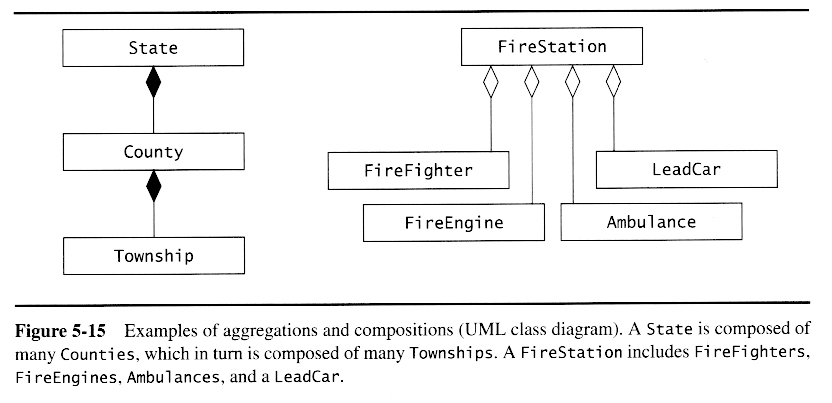
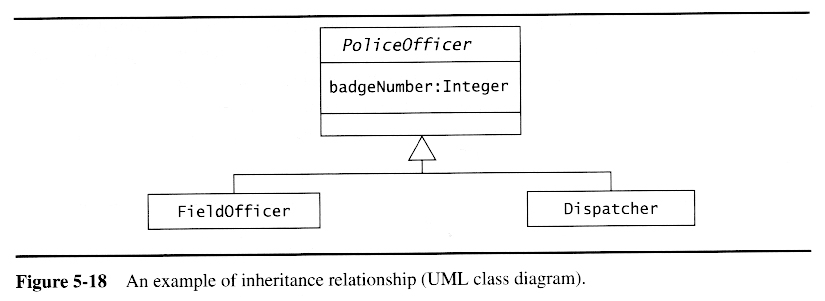
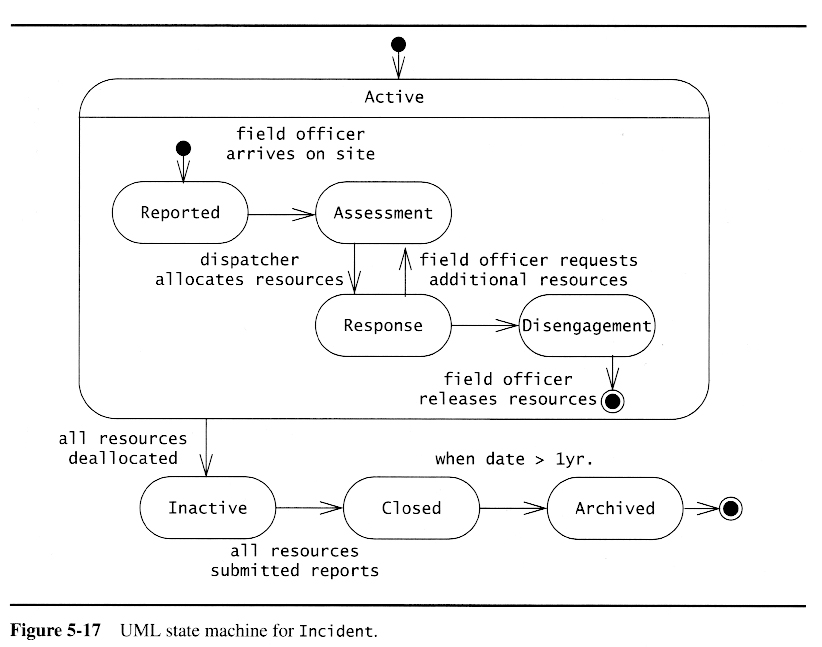
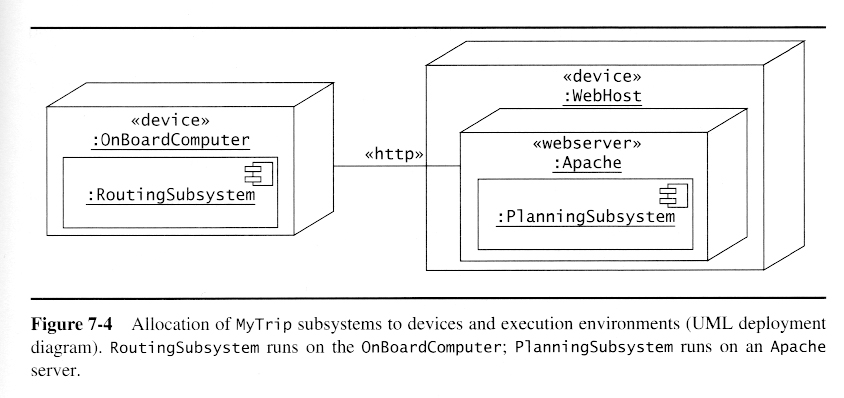
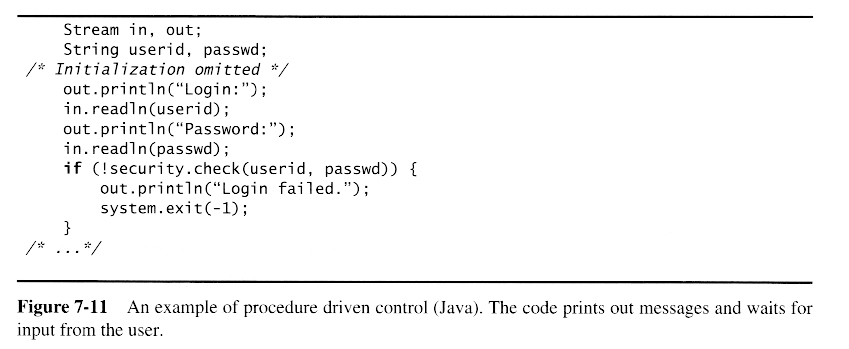
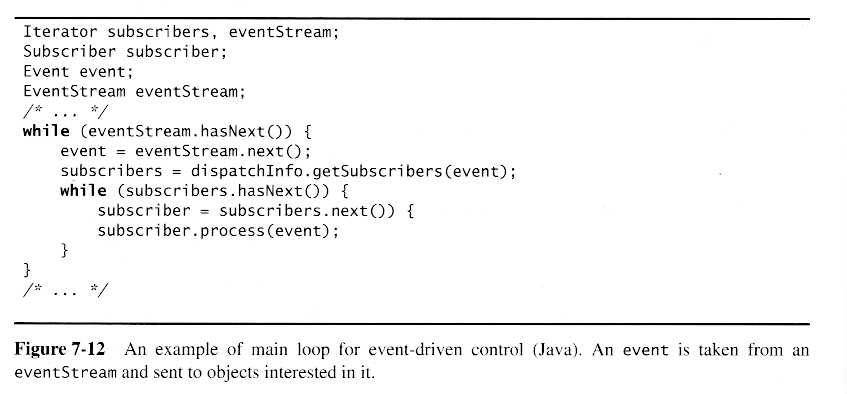
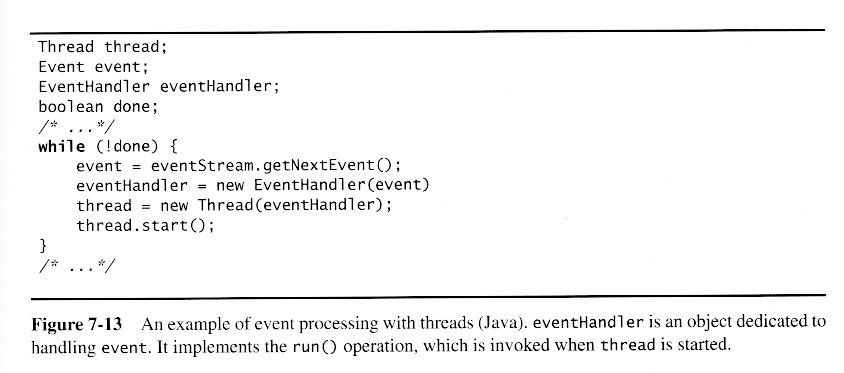
Once a preliminary set of classes and their relationships to each other have been identified, the next step is to break the overall system down into suitable subsystems, based on the structure of the class diagram, the semantics of the problem, and commonly used architectures.
Subsystems
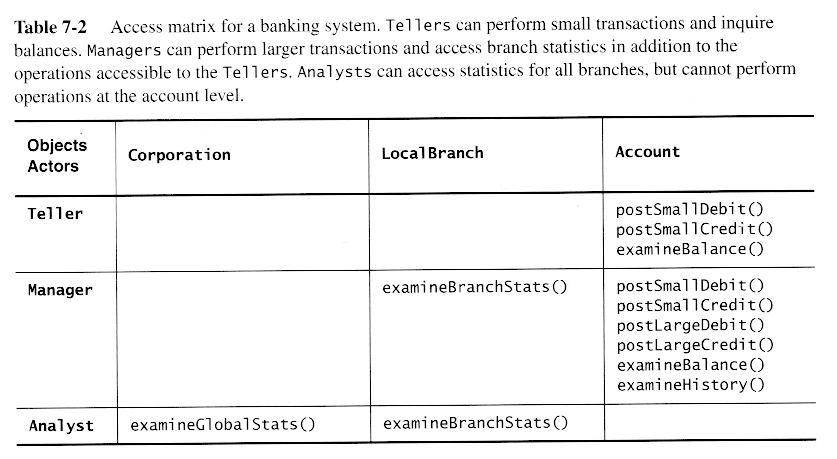
- A subsystem is a collection of classes that serves as a replaceable part of the system, with a well defined interface to the rest of the system, and a well-defined set of responsibilities or services provided by the subsystem.
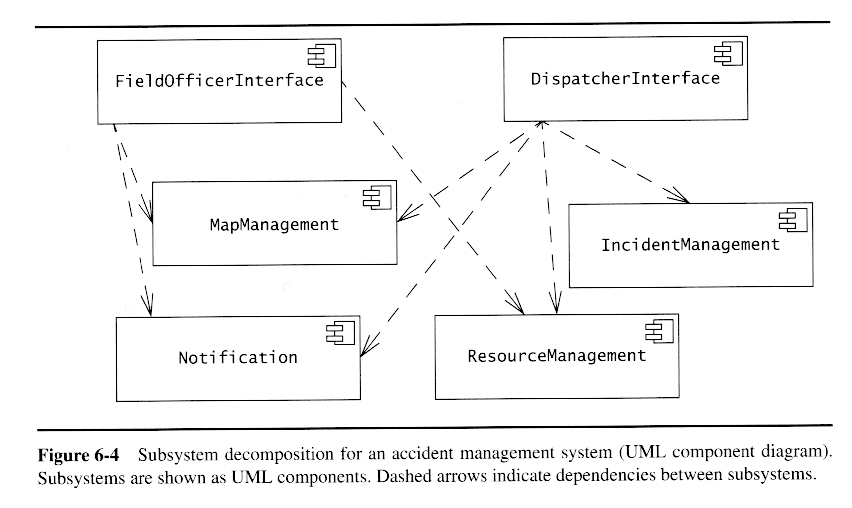
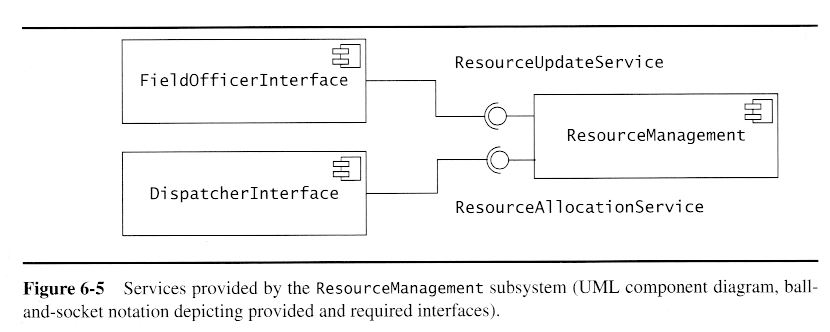
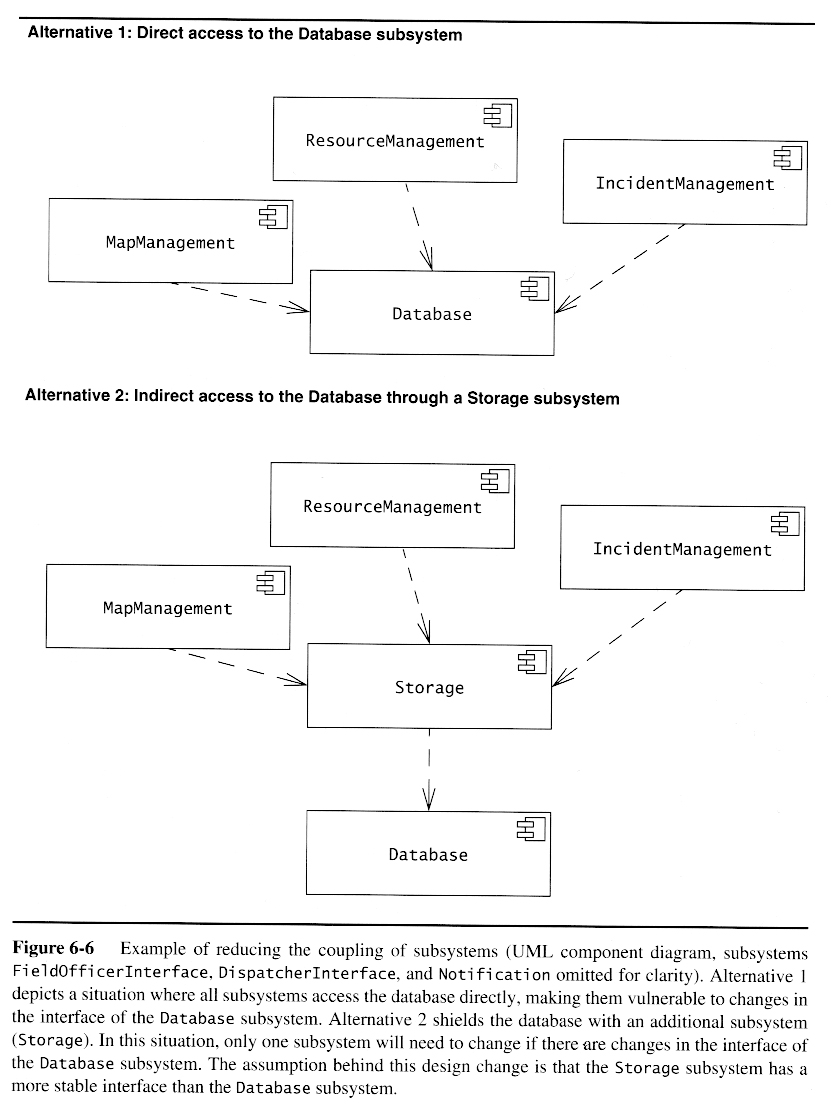
- Coupling is the connectedness betwen different subsystems. A good design will have minimal coupling.
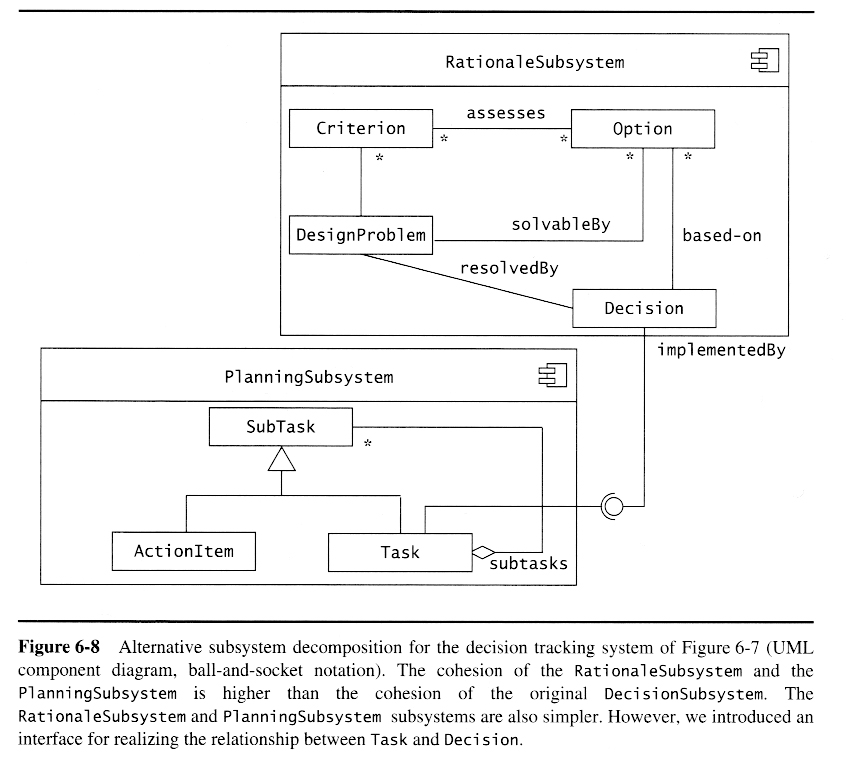
- Cohesion is the bonding of classes within a subsystem. A good design will have high cohesion.

Architectural Styles
- There are a number of well-known and commonly used approaches to organizing the subsystems of a system, known as architectural styles. Knowing, understanding, and using these styles can help produce better system designs.
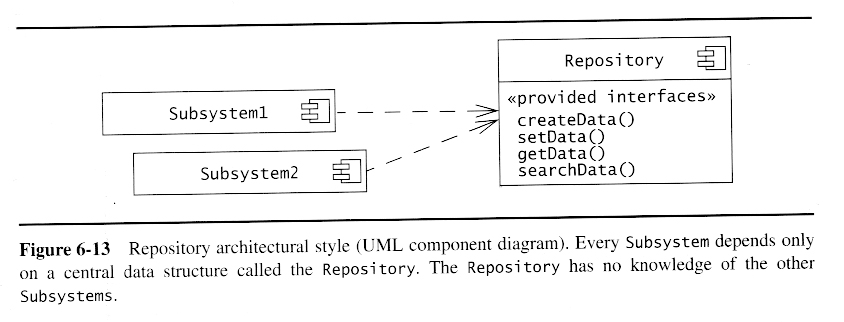
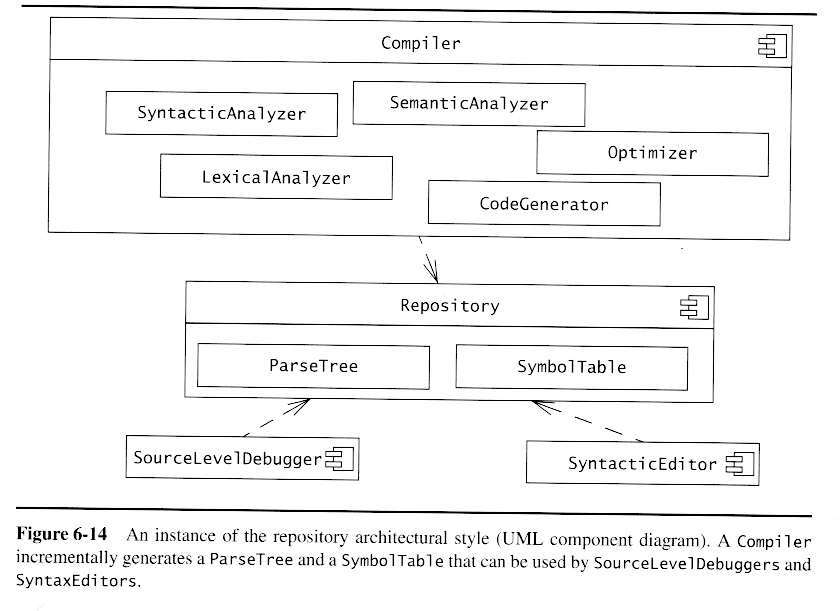
Repository
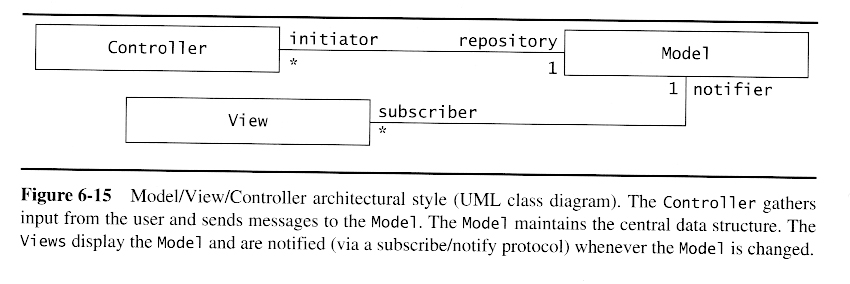
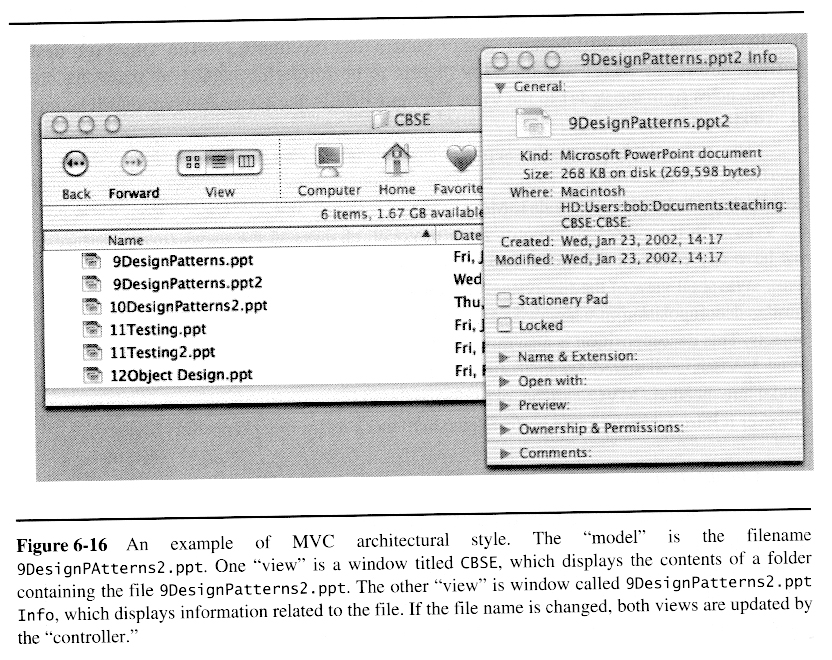
Model/View/Controller

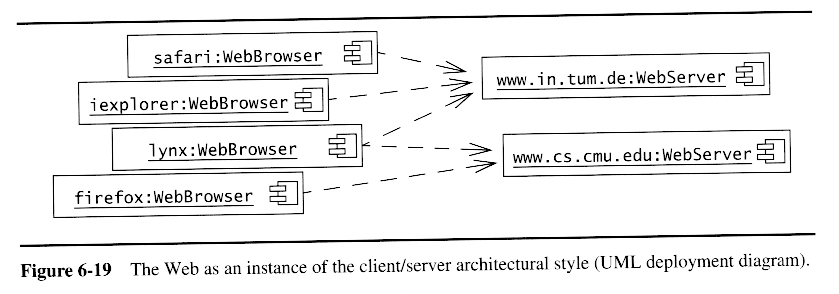
Client-Server

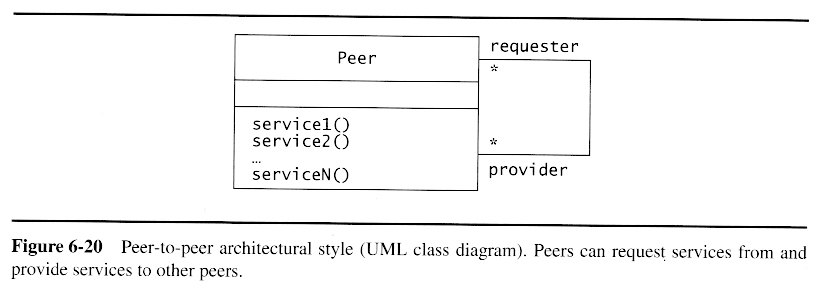
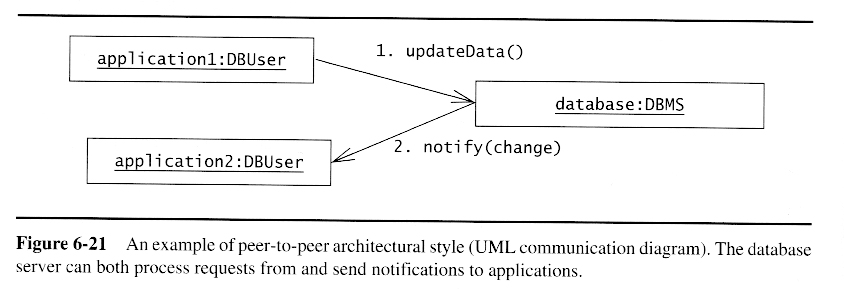
Peer-to-Peer
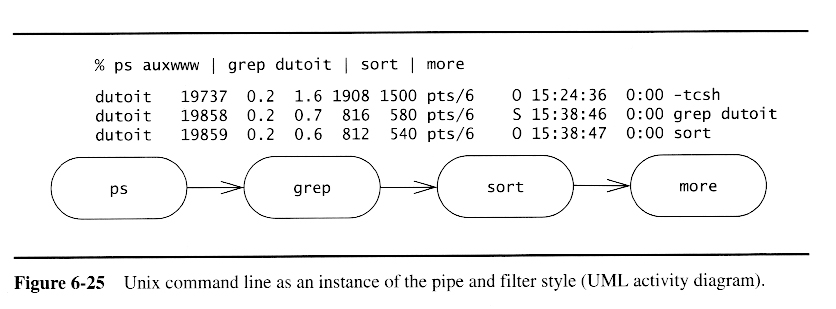
Pipe-and-Filter

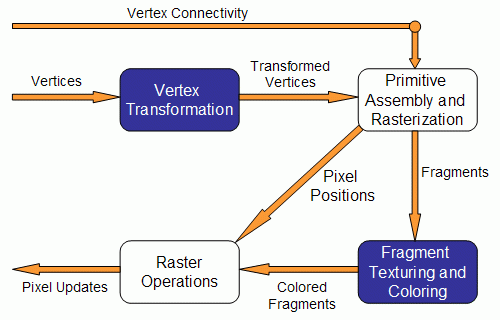
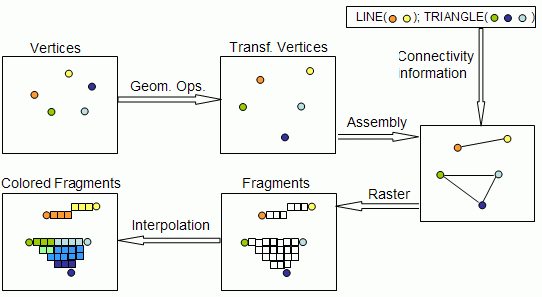
Example - The Open GL Graphics Processing Pipeline:
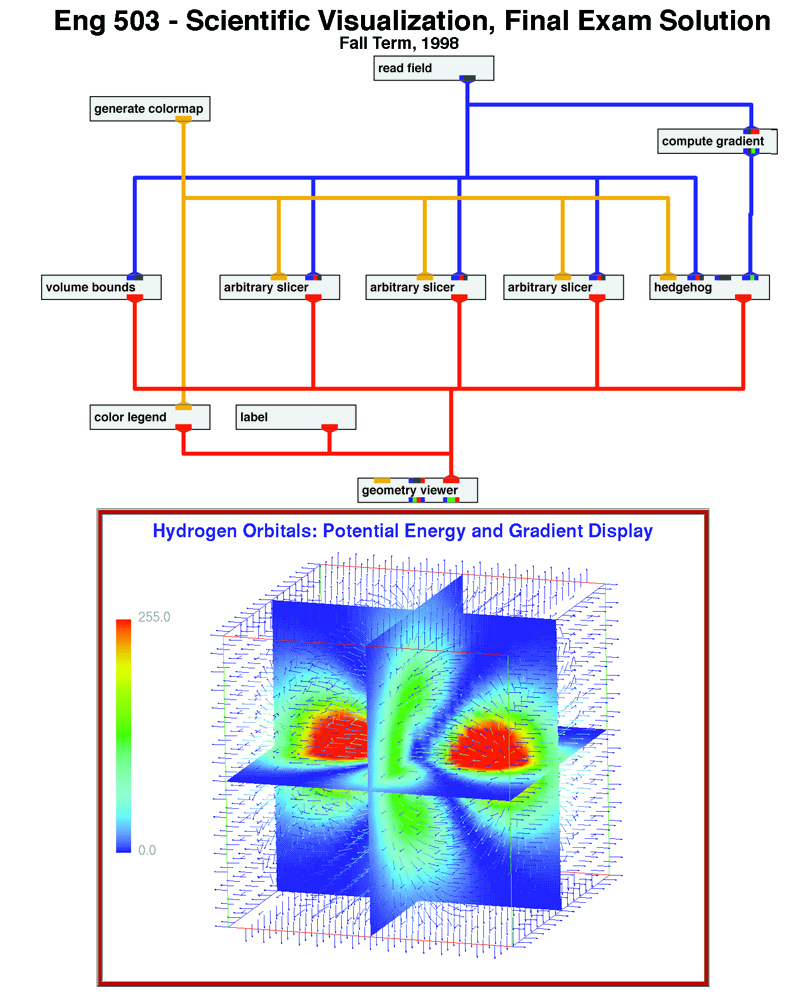
Example - Scientific Visualization with AVS:

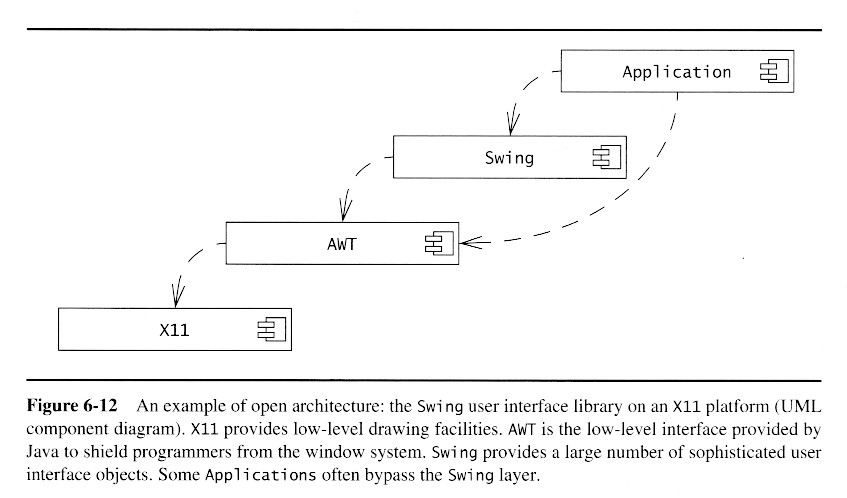
Layered Architectural Styles

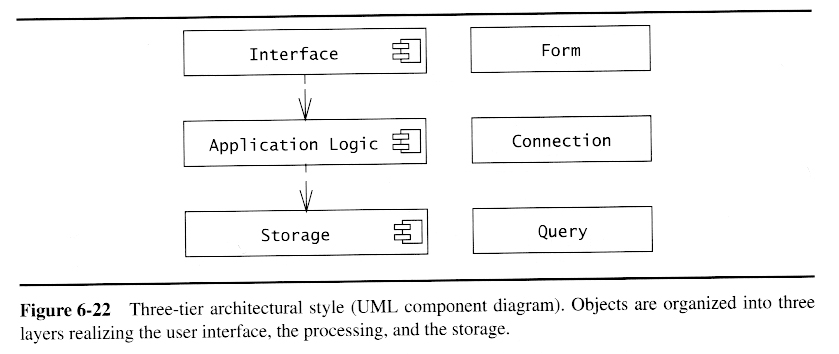
Three-Tier

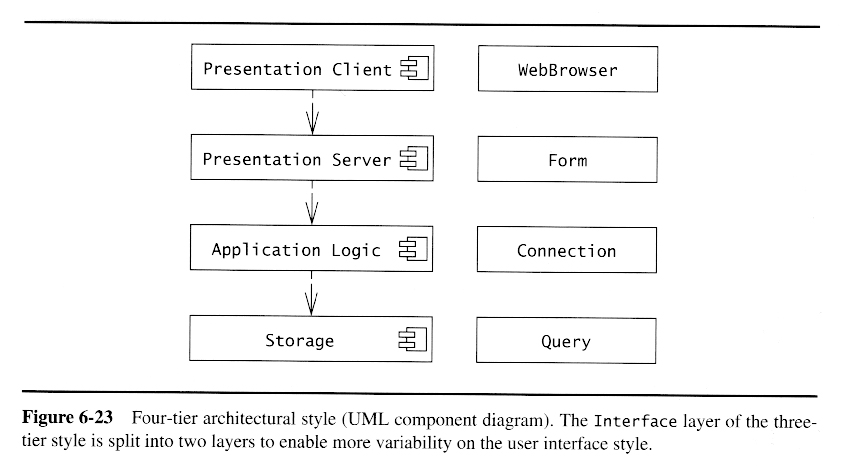
Four-Tier
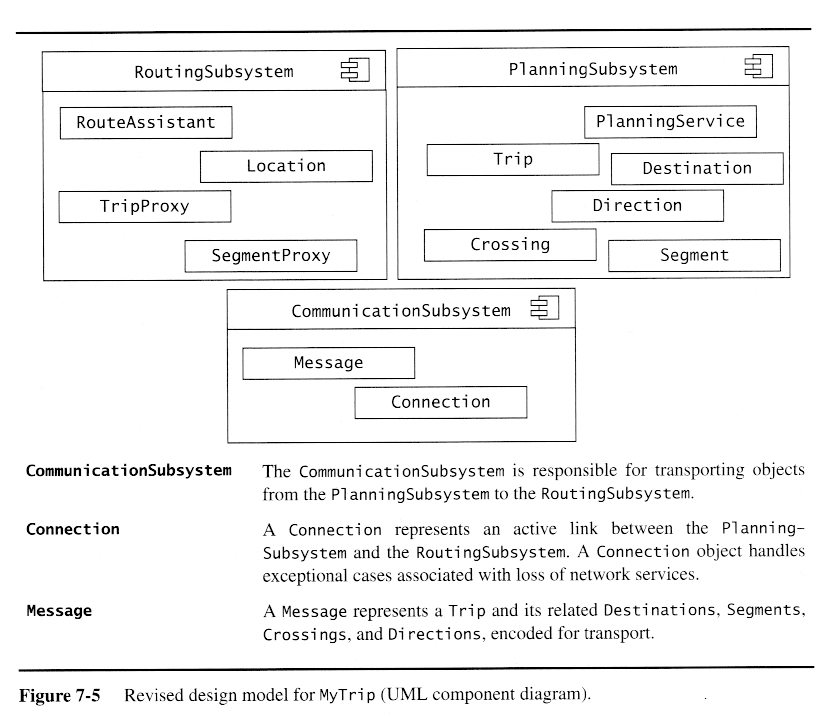
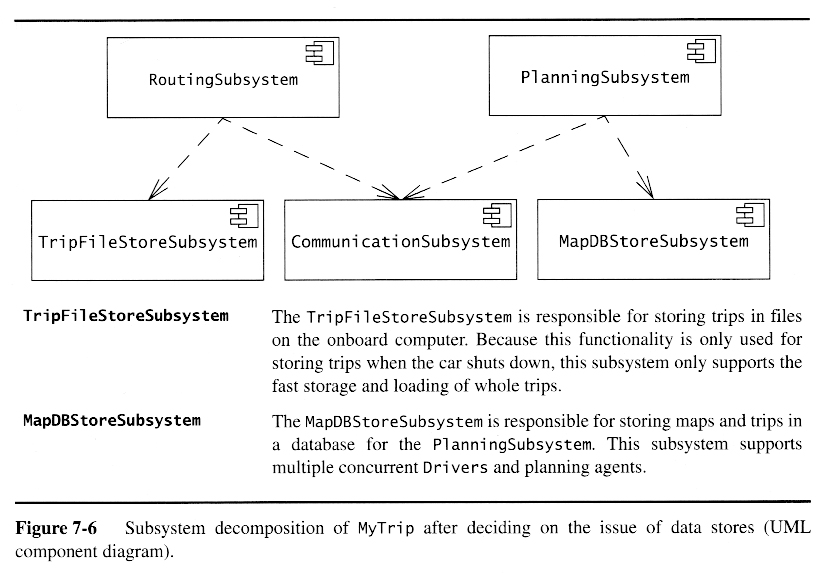
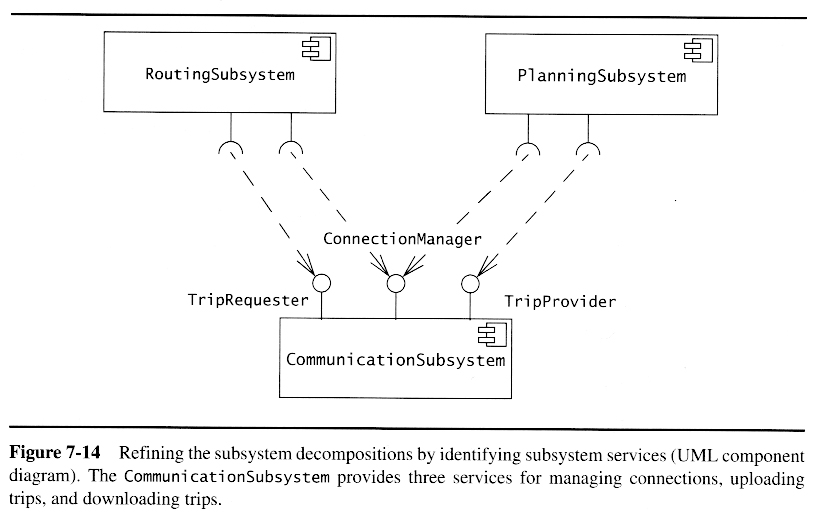
Example: From Objects to Subsystems
Starting Point: Analysis Model for a Route Planning System
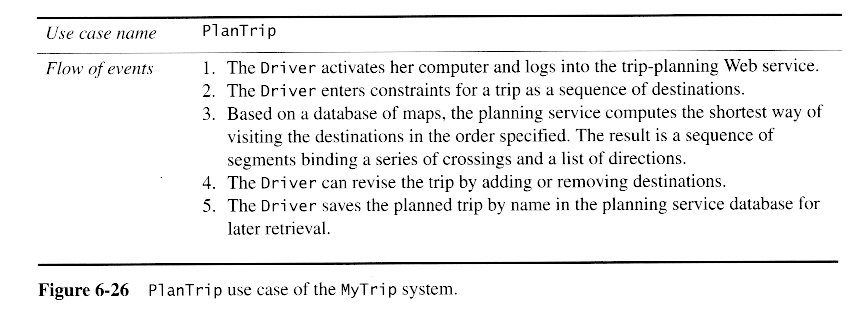
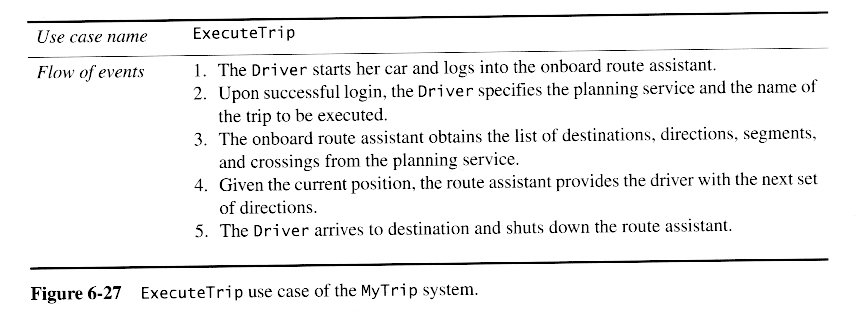

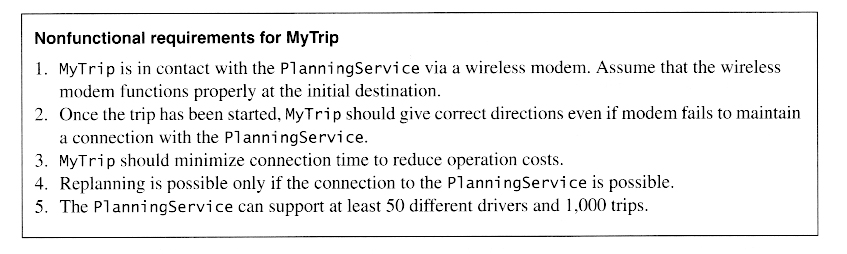
Identifying Design Goals ( See Below )
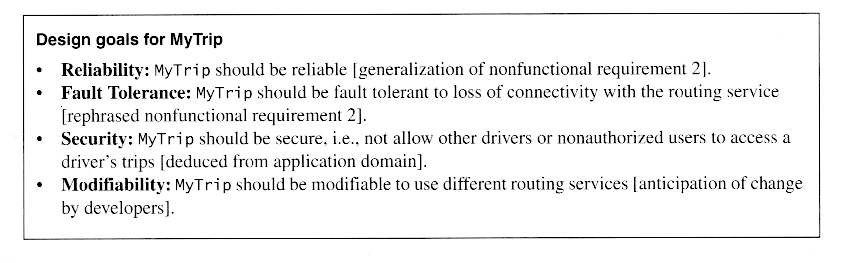
Identifying Subsystems

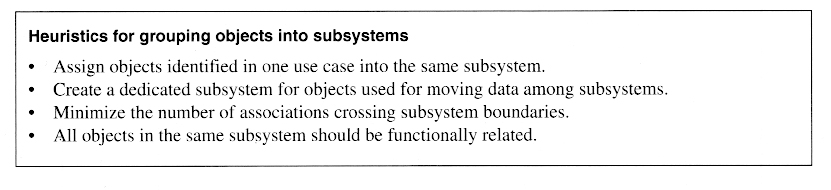
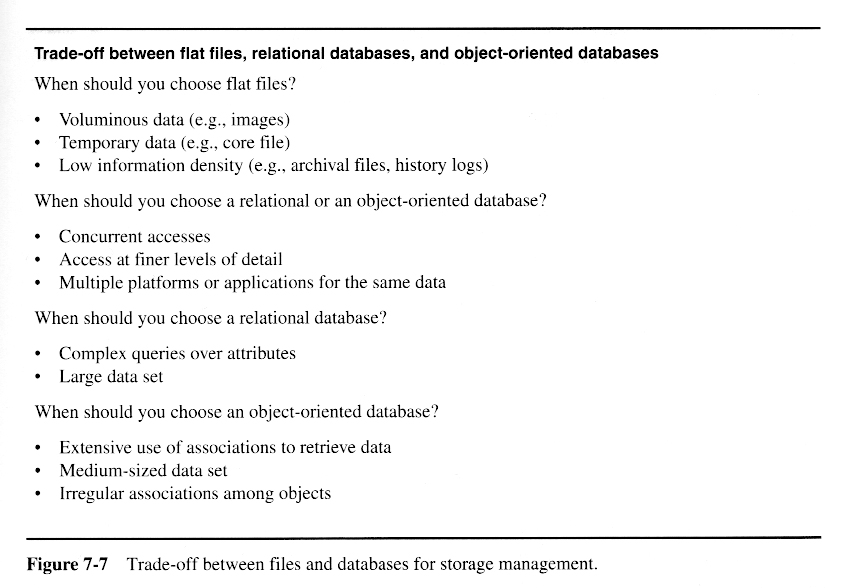
Adjusting and refining the design so as to optimize certain desirable properites, such as peformance, security, capacity, or resilience.