what i'm working on
hybrid value iteration for POMDPs
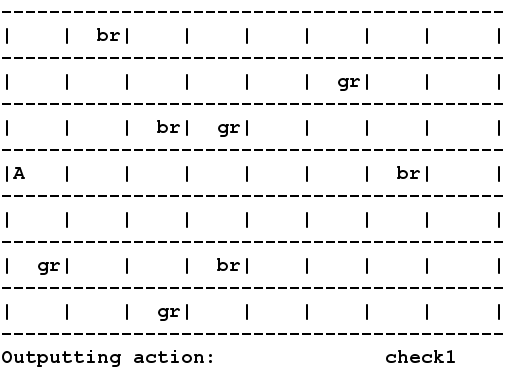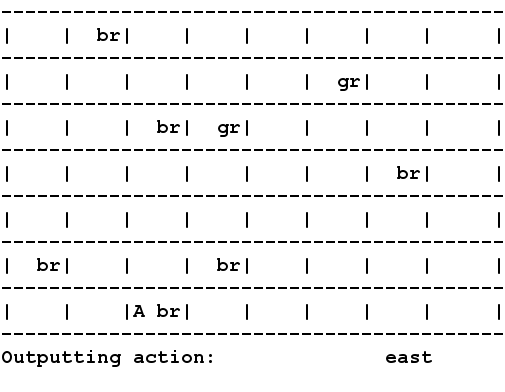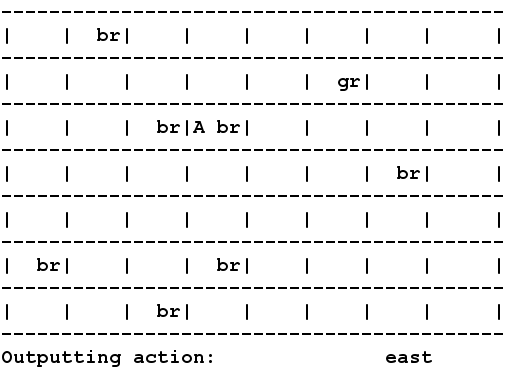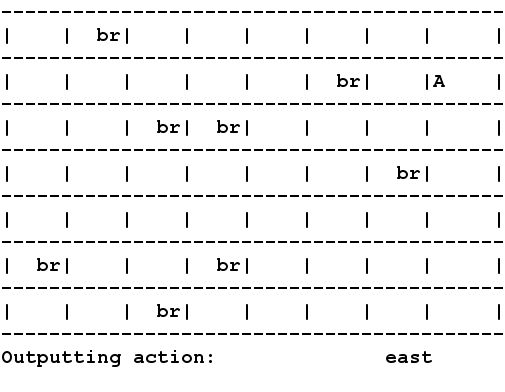 A drawback in several
online POMDP algorithms is that they never update the bounds that
have been computed offline. As an online agent expands its search
tree, it might be worthwhile to compute a backup operation and add
another alpha vector to the value function. Hybrid Value Iteration
(HYVI) is a hybrid algorithm that occasionally updates its
offline-computed bound on the value function to improve the obtained
reward while meeting real-time constraints. Shown in the picture you
see an agent "A" acting the in the RockSample domain using HYVI.
A drawback in several
online POMDP algorithms is that they never update the bounds that
have been computed offline. As an online agent expands its search
tree, it might be worthwhile to compute a backup operation and add
another alpha vector to the value function. Hybrid Value Iteration
(HYVI) is a hybrid algorithm that occasionally updates its
offline-computed bound on the value function to improve the obtained
reward while meeting real-time constraints. Shown in the picture you
see an agent "A" acting the in the RockSample domain using HYVI.
POMDP algorithms
 As first explained to me in CS411-AI1, a
part of AI studies the design of autonomous agents that interact
with their environments via sensors and actuators. I often visualize
this picture as a broad definition of the field, and one can think
of a Partially Observable Markov Decision Process (POMDP) as a
mathematical description of just that. I have been studying POMDP
solving techniques since I joined the MAS group, and this section of
the site is an ongoing effort to organize what I have learned so
far. More information here.
As first explained to me in CS411-AI1, a
part of AI studies the design of autonomous agents that interact
with their environments via sensors and actuators. I often visualize
this picture as a broad definition of the field, and one can think
of a Partially Observable Markov Decision Process (POMDP) as a
mathematical description of just that. I have been studying POMDP
solving techniques since I joined the MAS group, and this section of
the site is an ongoing effort to organize what I have learned so
far. More information here.
offline / online combination
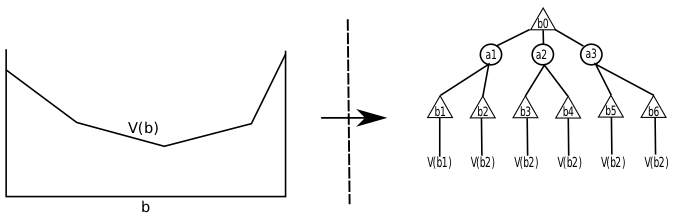 One of the many ways in which POMDP algorithms
can be classified is into offline and online methods. In this
project we try to derive general methodologies to design a hybrid
offline / online agent. Our aim is to invest the right amount of
computational power offline in order to leverage an online
implementation.
One of the many ways in which POMDP algorithms
can be classified is into offline and online methods. In this
project we try to derive general methodologies to design a hybrid
offline / online agent. Our aim is to invest the right amount of
computational power offline in order to leverage an online
implementation.
collaborative, computer-supported learning of animal communication
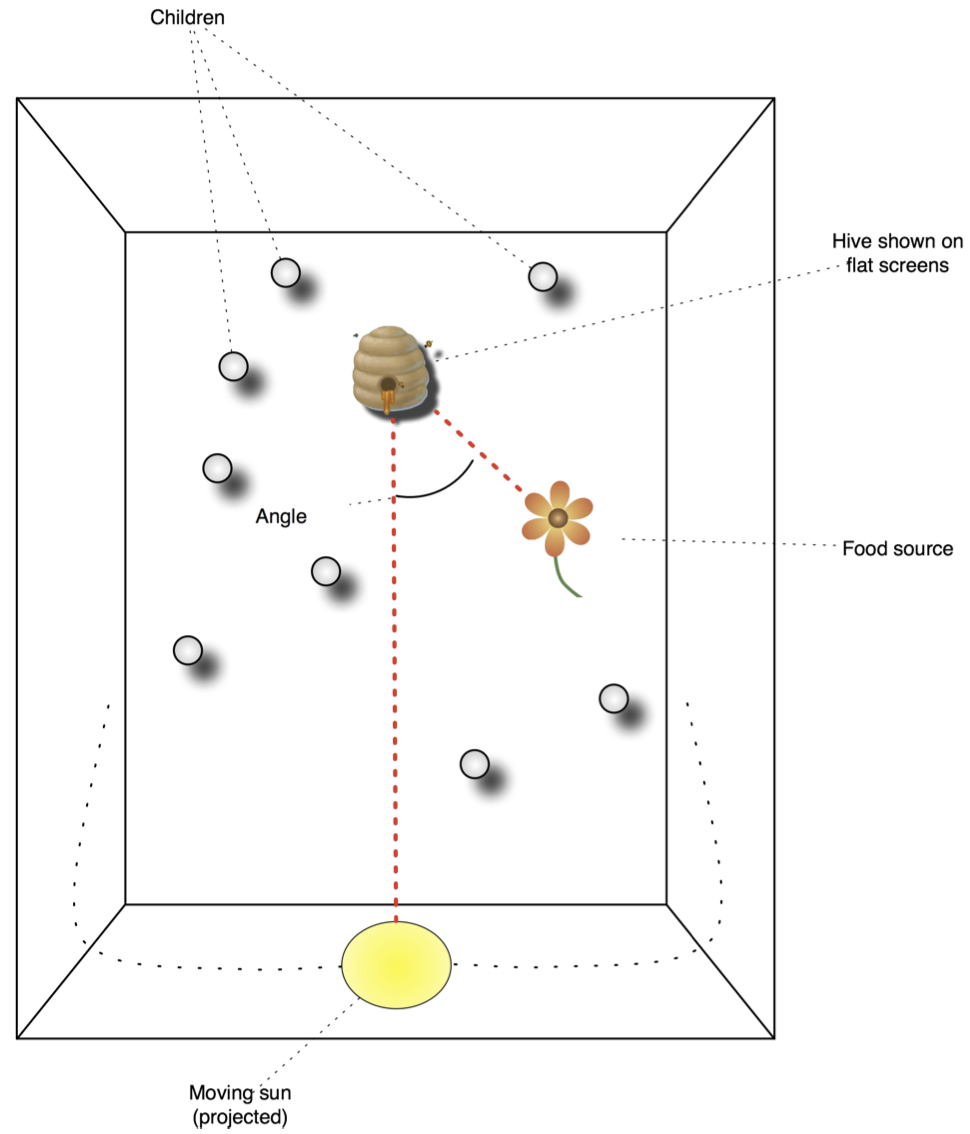 Contemporary goals of science education require that students
not only learn the facts and laws but instead understand science as
a principled process of inquiry. Students need to be part of
directing some of the inquiry and also participate in discussions.
In this work, we have designed a computer-supported activity that
introduces students to a unique example of animal communication. The
activity scaffolds the students' discovery of the bee tail-wagging
dance by guiding their inquiry process across four phases with the
help of goal directed group tasks, discussions, and experimentation.
The natural phenomenon of the tail-wagging dance stands as a unique
example of communication in the animal kingdom and its discovery is
a quintessential model of the scientific methodology. Middle school
students will be immersed in a virtual environment that allows them
to observe, hypothesize, experiment, and discuss findings connected
to the waggle dance. Aside from the mechanism of the dance itself,
our activity promotes learning about the scientific process, control
of multiple variables, polar coordinate systems, and teamwork.
Contemporary goals of science education require that students
not only learn the facts and laws but instead understand science as
a principled process of inquiry. Students need to be part of
directing some of the inquiry and also participate in discussions.
In this work, we have designed a computer-supported activity that
introduces students to a unique example of animal communication. The
activity scaffolds the students' discovery of the bee tail-wagging
dance by guiding their inquiry process across four phases with the
help of goal directed group tasks, discussions, and experimentation.
The natural phenomenon of the tail-wagging dance stands as a unique
example of communication in the animal kingdom and its discovery is
a quintessential model of the scientific methodology. Middle school
students will be immersed in a virtual environment that allows them
to observe, hypothesize, experiment, and discuss findings connected
to the waggle dance. Aside from the mechanism of the dance itself,
our activity promotes learning about the scientific process, control
of multiple variables, polar coordinate systems, and teamwork.
past projects
a study of password habits assessment methods
 A major
focus of human-computer interaction and security research has been
to strengthen systems providing sensitive services. Although
algorithmic advancements are necessary, overall security offered by
a system not only depend on the use of cryptography but also on the
humans interacting with it. Many researchers have found insecure
habits in the creation and maintenance of passwords, and have
regarded humans as the weakest link Several studies have made
important advances by studying existing systems, users’ attitudes
and habits. To avoid human limitations (memory, computation power)
researchers have also proposed new interesting authentication
systems. Most of these studies evaluate the efficacy of the
proposed systems against existing systems on characteristics like
password strength, reuse, etc. They often employ one of three
methods to capture human habits, namely: Standard Survey, Creation
Method and Real password analysis. Survey techniques gage habits by
posing several questions to users in relation to their
passwords. Creation techniques pose similar questions about a
password created on the spot. Real password studies, as the name
suggests, analyze actual passwords of users by means of software
tools such as agents deployed over the Internet. We present
empirical evidence that conventional data gathering techniques have
inherent weaknesses and collect incomparable data. We also propose a
new method to capture password-related data, called Direct Metrics,
that primarily avoids overly intrusive questions. Further, we
conclude with several recommendations for studies that aim to gather
password-related information from users.
A major
focus of human-computer interaction and security research has been
to strengthen systems providing sensitive services. Although
algorithmic advancements are necessary, overall security offered by
a system not only depend on the use of cryptography but also on the
humans interacting with it. Many researchers have found insecure
habits in the creation and maintenance of passwords, and have
regarded humans as the weakest link Several studies have made
important advances by studying existing systems, users’ attitudes
and habits. To avoid human limitations (memory, computation power)
researchers have also proposed new interesting authentication
systems. Most of these studies evaluate the efficacy of the
proposed systems against existing systems on characteristics like
password strength, reuse, etc. They often employ one of three
methods to capture human habits, namely: Standard Survey, Creation
Method and Real password analysis. Survey techniques gage habits by
posing several questions to users in relation to their
passwords. Creation techniques pose similar questions about a
password created on the spot. Real password studies, as the name
suggests, analyze actual passwords of users by means of software
tools such as agents deployed over the Internet. We present
empirical evidence that conventional data gathering techniques have
inherent weaknesses and collect incomparable data. We also propose a
new method to capture password-related data, called Direct Metrics,
that primarily avoids overly intrusive questions. Further, we
conclude with several recommendations for studies that aim to gather
password-related information from users.
 A drawback in several
online POMDP algorithms is that they never update the bounds that
have been computed offline. As an online agent expands its search
tree, it might be worthwhile to compute a backup operation and add
another alpha vector to the value function. Hybrid Value Iteration
(HYVI) is a hybrid algorithm that occasionally updates its
offline-computed bound on the value function to improve the obtained
reward while meeting real-time constraints. Shown in the picture you
see an agent "A" acting the in the RockSample domain using HYVI.
A drawback in several
online POMDP algorithms is that they never update the bounds that
have been computed offline. As an online agent expands its search
tree, it might be worthwhile to compute a backup operation and add
another alpha vector to the value function. Hybrid Value Iteration
(HYVI) is a hybrid algorithm that occasionally updates its
offline-computed bound on the value function to improve the obtained
reward while meeting real-time constraints. Shown in the picture you
see an agent "A" acting the in the RockSample domain using HYVI.
 One of the many ways in which POMDP algorithms
can be classified is into offline and online methods. In this
project we try to derive general methodologies to design a hybrid
offline / online agent. Our aim is to invest the right amount of
computational power offline in order to leverage an online
implementation.
One of the many ways in which POMDP algorithms
can be classified is into offline and online methods. In this
project we try to derive general methodologies to design a hybrid
offline / online agent. Our aim is to invest the right amount of
computational power offline in order to leverage an online
implementation.  Contemporary goals of science education require that students
not only learn the facts and laws but instead understand science as
a principled process of inquiry. Students need to be part of
directing some of the inquiry and also participate in discussions.
In this work, we have designed a computer-supported activity that
introduces students to a unique example of animal communication. The
activity scaffolds the students' discovery of the bee tail-wagging
dance by guiding their inquiry process across four phases with the
help of goal directed group tasks, discussions, and experimentation.
The natural phenomenon of the tail-wagging dance stands as a unique
example of communication in the animal kingdom and its discovery is
a quintessential model of the scientific methodology. Middle school
students will be immersed in a virtual environment that allows them
to observe, hypothesize, experiment, and discuss findings connected
to the waggle dance. Aside from the mechanism of the dance itself,
our activity promotes learning about the scientific process, control
of multiple variables, polar coordinate systems, and teamwork.
Contemporary goals of science education require that students
not only learn the facts and laws but instead understand science as
a principled process of inquiry. Students need to be part of
directing some of the inquiry and also participate in discussions.
In this work, we have designed a computer-supported activity that
introduces students to a unique example of animal communication. The
activity scaffolds the students' discovery of the bee tail-wagging
dance by guiding their inquiry process across four phases with the
help of goal directed group tasks, discussions, and experimentation.
The natural phenomenon of the tail-wagging dance stands as a unique
example of communication in the animal kingdom and its discovery is
a quintessential model of the scientific methodology. Middle school
students will be immersed in a virtual environment that allows them
to observe, hypothesize, experiment, and discuss findings connected
to the waggle dance. Aside from the mechanism of the dance itself,
our activity promotes learning about the scientific process, control
of multiple variables, polar coordinate systems, and teamwork.
