For Fun, not just for publication
A project on social influence maximization is accepted by CIKM2012.
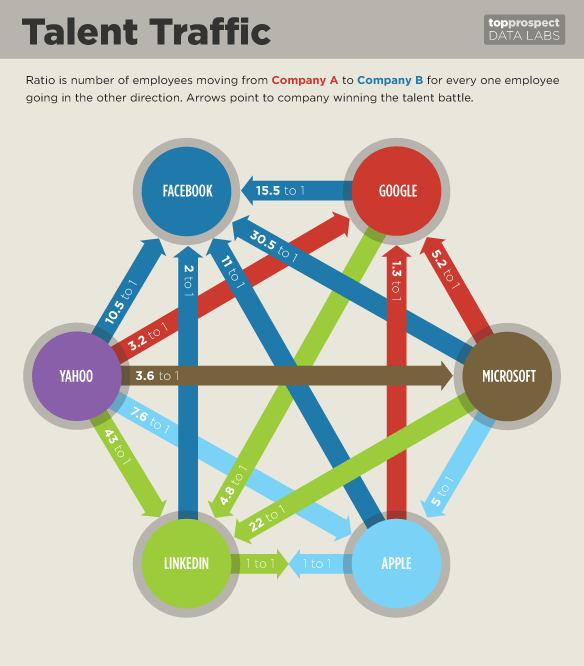 Another recent research project (Accepted by KDD2012):
Another recent research project (Accepted by KDD2012):
- What does this graph tell us?
- What if we have the companies from the whole industy?
- What theoretical abstraction can we establish?
- A paper answering these questions is under review
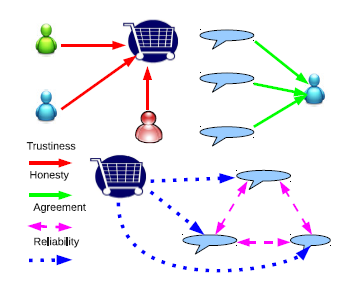 Detecting spam reviews and fake reviewers, as well as over-spammed online stores via Review Graph.
Detecting spam reviews and fake reviewers, as well as over-spammed online stores via Review Graph.
Online shopping reviews provide the valuable information for customers to compare the quality of products and store services
for potential purchases. However, spammers are joining this community trying to mislead consumers by writing fake or unfair reviews to confuse the public. We want to catch them! However, they are out of radar if we merely focus on what they wrote. Therefore,
we constructed this Review Graph to let the link structure speaks to defeat their disguise.
This research is a joint work with Dr. Bing Liu.
Furthermore, we studied how to catch singular review spammers who may have many fake accounts and only write one review per account.
See Sihong Xie's page for more information.
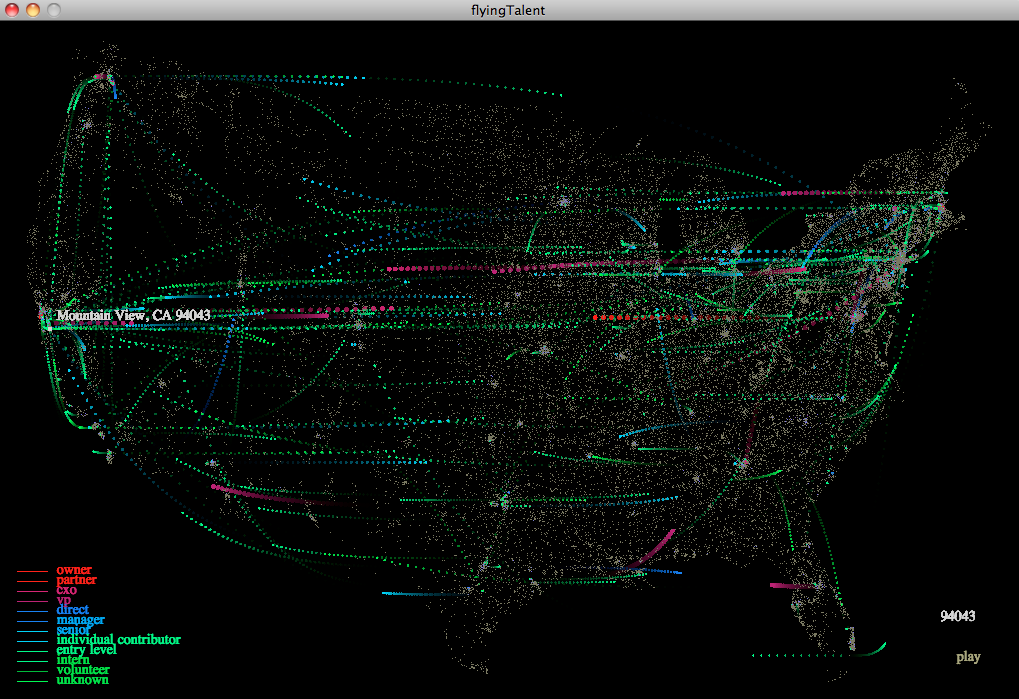
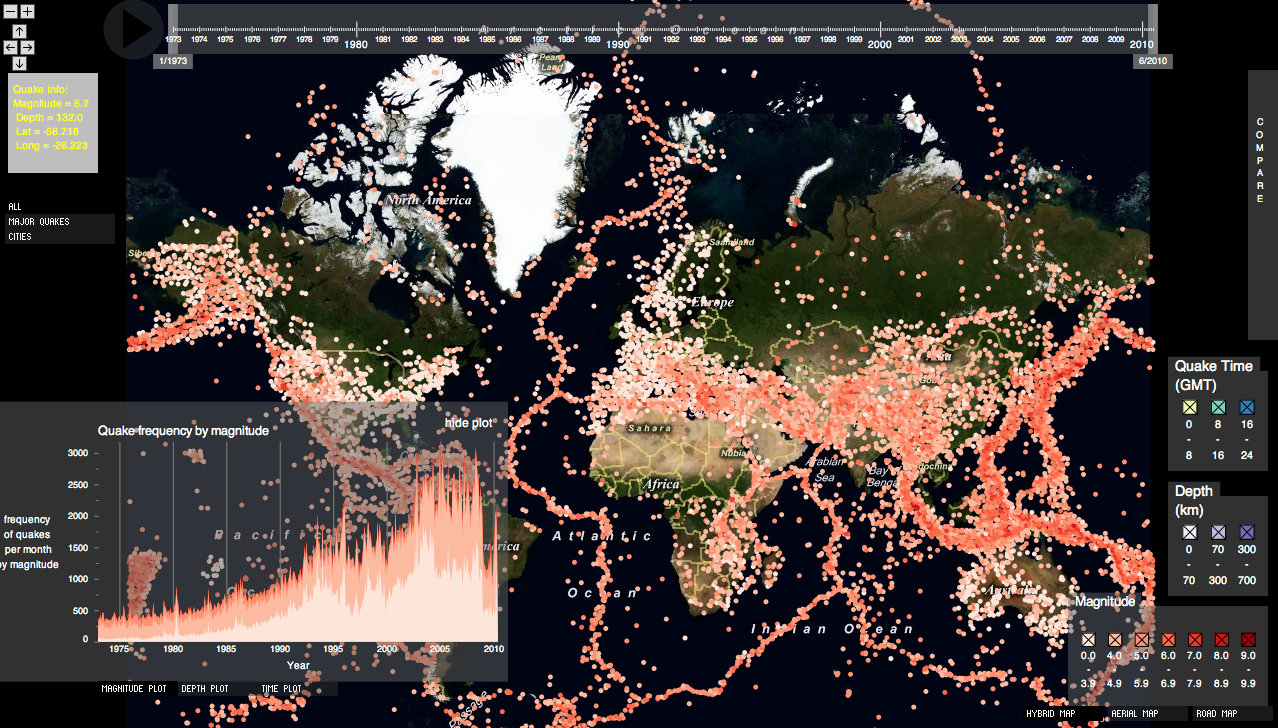
Information Visualization
One picture worth a thousand words. It is especially true in data mining and knowledge discovery. We are human. We are good at
understanding things in picture form, not numerical form. What makes us more comfortable is animations and wonderful sounds.
Here I demo two fantastic projects of visualization. The left one is an animation of American IT industry job changing flows in June, 2011.
It comes with encouraging music. The whole effect is aesthetic.
The right one is for exploration of earthquakes all over the world from 1970s to now. It is also animated. It was a joint course work with
Jillian Aurisano and Rohan Dargad.
Secure Two-party Sorting, Selection, and Permuting
Sorting, selection, and permuting are foundimental algorithmic routines. It goes without saying how important they are.
Numerous algorithms have been designed on doing these tasks efficiently. However, they are all on single party or plain text.
Consider a situation where two parties have an array of numbers each, but they do not want to disclose their numbers to the
other party. Their goal is to sort the numbers together (or select k-th largest, or do a permutation) without letting the
other party knowing any of numbers they are not supposed to know. It sounds twisty and impossible.
This project is the first one to solve this problem, with the most efficient algorithm to date.
This is a joint work with Tongbo Luo, Dr. Michael T. Goodrich, and
Dr. Wenliang Du.
Privacy-preserving Data Mining and Data Publishing
When data mining/publishing meets privacy concerns, there comes this interesting topic. I have three papers on this topic. But currently
I did not continue working on it. Maybe I will do interesting work about privacy again in the future.
 Another recent research project (Accepted by KDD2012):
Another recent research project (Accepted by KDD2012):
 Detecting spam reviews and fake reviewers, as well as over-spammed online stores via Review Graph.
Detecting spam reviews and fake reviewers, as well as over-spammed online stores via Review Graph. 

